Here I will be talking about configuring SSL wildcard certificates in IIS 6.0 on Win2k3 SP1 and above.
Setting up SSL with a SelfSSL certificate on Windows Server 2003. Now you will be presented with an overview, you can click 'Next' and the install will copy the selected files. When that's done, click 'Finish' Now we will create a certificate. Click Start - All Programs - IIS Resources - SelfSSL - SelfSSL Type 'selfssl /T'.
You may have a scenario wherein you want to have the same certificate installed for multiple Websites. Now in a normal scenarios this is not possible.
What I mean is you cannot have the same certificate installed on multiple Websites. To achieve a similar functionality you need to get a wildcard certificate from a Certificate Authority.
A wildcard certificate can be applied when you have the same end-domain name for all your Websites wherein you want to install the certificate.
Let's say you have Websites like www.test.com, mail.test.com and hrweb.test.com. Here the same end-domain name is present which is test.com.
Also remember that you can install the certificate for all such Websites when all of them are running under the same IP/Port combination. Here host headers will be the identifying criteria for Websites.
So let's say you have the following configuration:
WebSite Host Header Value IP Address Port SSL Port
Test1 www.test.com 10.0.1.1 80 443
Test2 mail.test.com 10.0.1.1 80 443
Test3 hrweb.test.com 10.0.1.1 80 443
and you want to use the same certificate for all the above Websites, Wildcard certificate is a viable option.
Here are the steps to obtain a wildcard certificate through IIS manager:
-In IIS Manager, expand the local computer, and then expand the Web Sites folder.
-Right-click the Web site for which you want to obtain a wildcard server certificate, and then click on Properties.
-On the Directory Security tab, under Secure communications Button, click Server Certificate.
-In the Web Server Certificate Wizard, click Create a new certificate.
-Follow the Web Server Certificate Wizard, which will guide you through the process of requesting a new server certificate. You can have any name in the Wizard which shows Name and Security Settings. On the 'Your Site's Common Name' page, type a name in the Common name box, using the following format:
*.<sitename> for example, *.test.com (as in our scenario).
By default, the certificate request file is saved as C:Certreq.txt, but the wizard allows you to specify a different location of your choice.
-Click Finish to complete the wizard.
After you receive the wildcard server certificate from the Certification Authority, assign the same certificate on all Web sites that have the same IP/port binding and are distinguished only by the host header name.

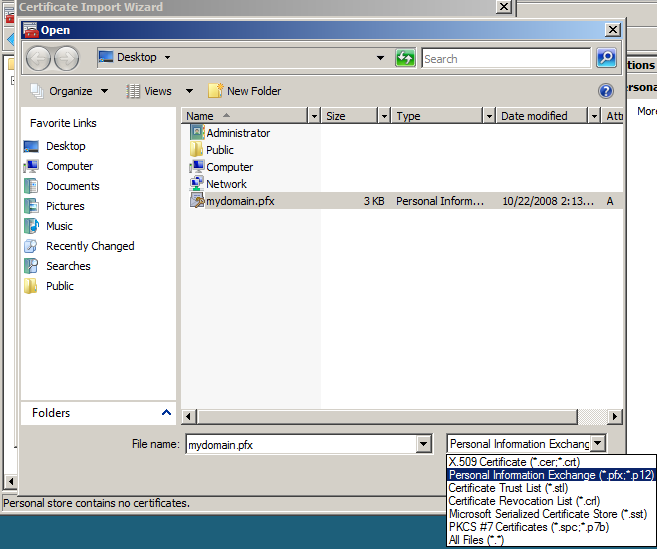
Here is a Screenshot of the wildcard certificate that we got for our *.test.com sites.
Now at this point if you try to access any of the Websites you will see that all of the HTTPS responses come from one specific site.
What I mean is that if you access https://www.test.com, https://mail.test.com or https://hrweb/test.com you will get the response from one site only.
You won't get the corresponding web pages from different Websites depending upon the site in URL. You will also see that only one of the Websites will be running. Other Websites will be in stopped state because we cannot have multiple Websites running with same IP and same SSL port binding (without of course some extra settings). If you try to start the other Websites you may see something like this below:
Windows Server 2003 Install Ssl Certificate Iis
Now, the next most important thing is to follow the script below:
Go to Start Menu, click Run, type 'cmd', and then click OK.
Install Certificate Windows Server 2012
Type the following command at the command prompt:
C:InetpubAdminScripts>cscript.exe adsutil.vbs set /w3svc/<site identifier>/SecureBindings ':443:<host header>' <--- [It's not case sensitive]
where host header is the host header for the Web site, for example, www.test.com or mail.test.com.
e.g.
C:InetpubAdminScripts>cscript.exe adsutil.vbs set /w3svc/1/SecureBindings ':443:www.test.com'
C:InetpubAdminScripts>cscript.exe adsutil.vbs set /w3svc/2/SecureBindings ':443:mail.test.com'
C:InetpubAdminScripts>cscript.exe adsutil.vbs set /w3svc/3/SecureBindings ':443:hrweb.test.com'
Now once we have these settings in place for the Websites you should be able to browse to the Websites. You will also be able to start all the Websites without any issues.
Ensure that you do not modify any of the SSL related settings in the IIS manager like host header etc. after doing the changes in the metabase.
Finally have SSLDiag handy in case you get into issues for any general SSL related troubleshooting 🙂
-->When creating a self-hosted Windows Communication Foundation (WCF) service with the WSHttpBinding class that uses transport security, you must also configure a port with an X.509 certificate. If you are not creating a self-hosted service, you can host your service on Internet Information Services (IIS). For more information, see HTTP Transport Security.
Windows Server Install Certificate
To configure a port, the tool you use depends on the operating system that is running on your machine.
If you are running Windows Server 2003 or Windows XP, use the HttpCfg.exe tool. With Windows Server 2003 this tool is installed. With Windows XP, you can download the tool at Windows XP Service Pack 2 Support Tools. For more information, see Httpcfg Overview. The Windows Support Tools documentation explains the syntax for the Httpcfg.exe tool.
If you are running Windows Vista, use the Netsh.exe tool that is already installed.
This topic describes how to accomplish several procedures:
Determining a computer's current port configuration.
Getting a certificate's thumbprint (necessary for the following two procedures).
Binding an SSL certificate to a port configuration.
Binding an SSL certificate to a port configuration and supporting client certificates.
Deleting an SSL certificate from a port number.
Note that modifying certificates stored on the computer requires administrative privileges.
To determine how ports are configured
In Windows Server 2003 or Windows XP, use the HttpCfg.exe tool to view the current port configuration, using the query and ssl switches, as shown in the following example.
In Windows Vista, use the Netsh.exe tool to view the current port configuration, as shown in the following example.
To get a certificate's thumbprint
Use the Certificates MMC snap-in to find an X.509 certificate that has an intended purpose of client authentication. For more information, see How to: View Certificates with the MMC Snap-in.
Access the certificate's thumbprint. For more information, see How to: Retrieve the Thumbprint of a Certificate.
Copy the thumbprint of the certificate into a text editor, such as Notepad.
Remove all spaces between the hexadecimal characters. One way to accomplish this is to use the text editor's find-and-replace feature and replace each space with a null character.
To bind an SSL certificate to a port number
In Windows Server 2003 or Windows XP, use the HttpCfg.exe tool in 'set' mode on the Secure Sockets Layer (SSL) store to bind the certificate to a port number. The tool uses the thumbprint to identify the certificate, as shown in the following example.
The -i switch has the syntax of
IP:portand instructs the tool to set the certificate to port 8012 of the computer. Optionally, the four zeroes that precede the number can also be replaced by the actual IP address of the computer.The -h switch specifies the thumbprint of the certificate.
In Windows Vista, use the Netsh.exe tool, as shown in the following example.
The certhash parameter specifies the thumbprint of the certificate.
The ipport parameter specifies the IP address and port, and functions just like the -i switch of the Httpcfg.exe tool described.
The appid parameter is a GUID that can be used to identify the owning application.
To bind an SSL certificate to a port number and support client certificates
In Windows Server 2003 or Windows XP, to support clients that authenticate with X.509 certificates at the transport layer, follow the preceding procedure but pass an additional command-line parameter to HttpCfg.exe, as shown in the following example.
The -f switch has the syntax of
nwhere n is a number between 1 and 7. A value of 2, as shown in the preceding example, enables client certificates at the transport layer. A value of 3 enables client certificates and maps those certificates to a Windows account. See HttpCfg.exe Help for the behavior of other values.In Windows Vista, to support clients that authenticate with X.509 certificates at the transport layer, follow the preceding procedure, but with an additional parameter, as shown in the following example.
To delete an SSL certificate from a port number
Use the HttpCfg.exe or Netsh.exe tool to see the ports and thumbprints of all bindings on the computer. To print the information to disk, use the redirection character '>', as shown in the following example.
In Windows Server 2003 or Windows XP, use the HttpCfg.exe tool with the delete and ssl keywords. Use the -i switch to specify the
IP:portnumber, and the -h switch to specify the thumbprint.In Windows Vista, use the Netsh.exe tool, as shown in the following example.
Example
The following code shows how to create a self-hosted service using the WSHttpBinding class set to transport security. When creating an application, specify the port number in the address.