Mar 07, 2014 SCCM Software Update PART 2 – Software Update Point configuration Posted by: Romain Serre in Configuration Manager March 7, 2014 4 Comments 42,814 Views SCCM Software Update PART 1 – Introduction to SCCM and WSUS. Configuration Manager Software Update Point Error 0X80073633 Invalid certificate signature. In my SCCM environment (1610 CB with last updates) I get error 0.
~ Bindusar Kushwaha
Hi everyone, Bindusar here again. Are you planning to install the System Center 2012 Configuration Manager (ConfigMgr 2012) client using a Software Update Point but running into issues? Below are the things you may want to check.
- The computer should be joined to the domain.
- Group Policy should be working properly.
- The Software Update Point should be installed and working properly.
- Configuration Manager should be published in Active Directory (AD).
- The Windows Update agent on client machines should be working properly.
- Client Push installation should not be configured.
When installing the client using a Software Update Point, we need to make sure a few things are configured:
- Configure the WSUS server location using Group Policy so that client machines can get ccmsetup as an update patch.
- From the Configuration Manager console, client installation should be configured using the Software Update Point.
That’s it!
You can find more information on this in the following articles:
How to Install Configuration Manager Clients Using Software Update Point Based Installation: http://technet.microsoft.com/en-us/library/bb633194.aspx
Top 3 ConfigMgr 2012 Client Installation Methods: http://blogs.technet.com/b/smartinez/archive/2013/09/27/top-3-configmgr-2012-client-installation-methods.aspx
Putting it all together
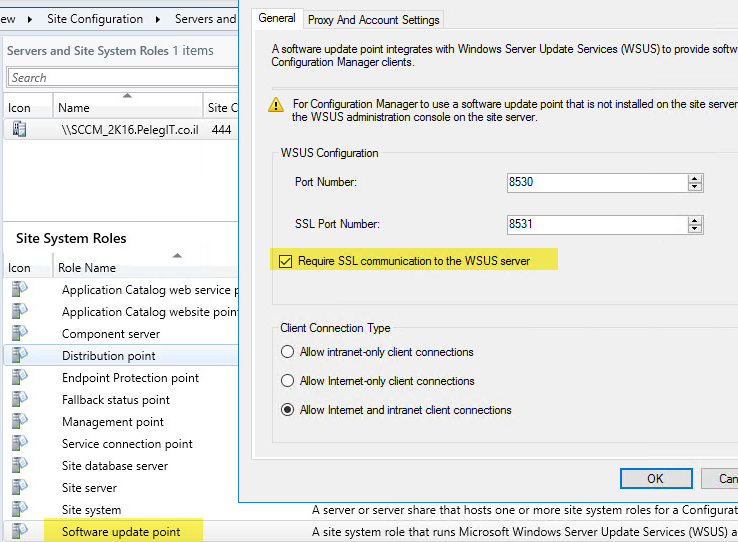
Configure Group Policy to locate the WSUS server by configuring the policy item named “Specify intranet Microsoft Update service location” and provide the WSUS server name (e.g. http://WsusServerName>:Port).
Then just run Gpupdate /force on the client and make sure it’s getting that policy (this can be checked using RSOP.msc).
At this point the client computer is now ready to get all the updates needed from WSUS server location.
Now it’s time to configure Configuration Manager to distribute the Client Installer package.
NOTE The “Published version” will be blank if it was NOT configured (published) earlier.
In WCM.log we can see the following lines:
Attempting connection to WSUS server: BinPri1.Contoso.com, port: 8530, useSSL: FalseSMS_WSUS_CONFIGURATION_MANAGER5/28/2014 4:07:24 AM4404 (0x1134)
Successfully connected to server: BinPri1.Contoso.com, port: 8530, useSSL: FalseSMS_WSUS_CONFIGURATION_MANAGER5/28/2014 4:07:24 AM4404 (0x1134)
Found published client Configuration Manager Client (5.00.7958.1000) (id=8427071a-da80-48c3-97de-c9c528f73a2d, version=5.00.7958.1000)SMS_WSUS_CONFIGURATION_MANAGER5/28/2014 4:07:24 AM4404 (0x1134)
Successful published and approved package 8427071A-DA80-48C3-97DE-C9C528F73A2D for Install to All Computers, Deadline UTC time=5/26/2014 9:53:43 PMSMS_WSUS_CONFIGURATION_MANAGER5/28/2014 4:07:24 AM4404 (0x1134)
completed checking for client deploymentSMS_WSUS_CONFIGURATION_MANAGER5/28/2014 4:07:24 AM4404 (0x1134)
Waiting for changes for 60 minutesSMS_WSUS_CONFIGURATION_MANAGER5/28/2014 4:07:24 AM4404 (0x1134)
As we can see, the update is not only published but it’s approved with a deadline automatically! Once we are able to see this line in WCM.log we are done from the server side.
Connect to SUSDB and you should be able to see the following now available:
If you are connecting to WSUS on Server 2008 R2 use .pipemssql$microsoft##sseesqlquery
If you are connecting to WSUS on Server 2012, use .pipeMICROSOFT##WIDtsqlquery
Now we need to wait and watch on the client machine for it to start the update scan cycle. Alternatively, you can manually trigger it from Control Panel with the Check for Updates option.
2014-05-2703:40:01:788936438Agent* Added update {8427071A-DA80-48C3-97DE-C9C528F73A2D}.1 to search result
2014-05-2703:40:01:788936438Agent* Found 1 updates and 72 categories in search; evaluated appl. rules of 265 out of 519 deployed entities
2014-05-2703:40:01:804936e78AU>>##RESUMED## AU: Search for updates [CallId = {A7DDCEFB-825C-4B67-949F-D92645D11D82}]
2014-05-2703:40:01:804936e78AU# 1 updates detected
2014-05-2703:40:01:804936e78AUAuto-approving update for download, updateId = {8427071A-DA80-48C3-97DE-C9C528F73A2D}.1, ForUx=0, IsOwnerUx=0, HasDeadline=1, IsMinor=0
2014-05-2703:40:01:804936e78AUAuto-approved 1 update(s) for download (NOT for Ux)
2014-05-2703:40:01:804936e78AU## START ##AU: Download updates
2014-05-2703:40:01:804936e78AU# Approved updates = 1
2014-05-2703:40:01:866936e78AUAU initiated download, updateId = {8427071A-DA80-48C3-97DE-C9C528F73A2D}.1, callId = {9057EBE8-6221-4213-AA08-4EA1E0820662}
2014-05-2703:40:01:866936e78AUSetting AU scheduled install time to 2014-05-27 21:30:00
2014-05-2703:40:01:866936e78AUAU setting pending client directive to 'Download Progress'
2014-05-2703:40:01:866936e78AU# Pending download calls = 1
2014-05-2703:40:01:866936e78AU<<## SUBMITTED ## AU: Download updates
2014-05-2703:40:01:991936438DnldMgr** START **DnldMgr: Downloading updates [CallerId = AutomaticUpdates]
2014-05-2703:40:01:991936438DnldMgr* Call ID = {9057EBE8-6221-4213-AA08-4EA1E0820662}
2014-05-2703:40:01:991936438DnldMgr* Priority = 3, Interactive = 0, Owner is system = 1, Explicit proxy = 0, Proxy session id = -1, ServiceId = {3DA21691-E39D-4DA6-8A4B-B43877BCB1B7}
2014-05-2703:40:01:991936438DnldMgr* Updates to download = 1
2014-05-2703:40:01:991936438Agent*Title = Configuration Manager Client (5.00.7958.1000)
2014-05-2703:40:01:991936438Agent*UpdateId = {8427071A-DA80-48C3-97DE-C9C528F73A2D}.1
2014-05-2703:40:02:038936438DnldMgr***********DnldMgr: New download job [UpdateId = {8427071A-DA80-48C3-97DE-C9C528F73A2D}.1]***********
2014-05-2703:40:02:585936438DnldMgr* BITS job initialized, JobId = {06E96DA6-6051-4A9D-B2EE-F58462B647F1}
2014-05-2703:40:02:741936438DnldMgr* Downloading from http://binpri1:8530/Content/E4/28F170F0C414D9474A43A4CAEB2577F2F8C86CE4.cab to C:WindowsSoftwareDistributionDownload222661f20b633750ff74f33b134f79d928f170f0c414d9474a43a4caeb2577f2f8c86ce4 (full file).
2014-05-2703:40:02:913936e78AUAU checked download status and it changed: Downloading is paused
2014-05-2703:40:02:975936e78AUAU checked download status and it changed: Downloading is not paused
2014-05-2703:40:02:975936e78AUAU setting pending client directive to 'Download Progress'
2014-05-2703:40:03:2889367f8DnldMgrBITS job {06E96DA6-6051-4A9D-B2EE-F58462B647F1} completed successfully
2014-05-2703:40:03:3979367f8MiscValidating signature for C:WindowsSoftwareDistributionDownload222661f20b633750ff74f33b134f79d928f170f0c414d9474a43a4caeb2577f2f8c86ce4:
2014-05-2703:40:03:4139367f8MiscMicrosoft signed: Yes
2014-05-2703:40:03:4299367f8DnldMgrDownload job bytes total = 611893, bytes transferred = 611893
2014-05-2703:40:03:4919367f8DnldMgr***********DnldMgr: New download job [UpdateId = {8427071A-DA80-48C3-97DE-C9C528F73A2D}.1]***********
2014-05-2703:40:03:4919367f8DnldMgr* All files for update were already downloaded and are valid.
2014-05-2703:40:03:632936e78AU>>##RESUMED## AU: Download update [UpdateId = {8427071A-DA80-48C3-97DE-C9C528F73A2D}, succeeded]
2014-05-2703:40:03:632936e78AU##END##AU: Download updates
2014-05-2703:40:03:632936e78AUAU setting pending client directive to 'Install Approval'
2014-05-2703:40:03:647936b04AUForced install timer expired for deadline install
2014-05-2703:40:03:647936b04AUUpdateDownloadProperties: 0 download(s) are still in progress.
2014-05-2703:40:03:647936b04AU## START ##AU: Install updates
2014-05-2703:40:03:647936b04AU# Initiating deadline install
2014-05-2703:40:03:647936b04AU# Approved updates = 1
2014-05-2703:40:03:647936b04AU<<## SUBMITTED ## AU: Install updates / installing updates [CallId = {08F360A4-EBDB-4097-BE41-1FDC1C683F65}]
2014-05-2703:40:03:6479369f0AUGetting featured update notifications.fIncludeDismissed = true
2014-05-2703:40:03:6479369f0AUNo featured updates available.
2014-05-2703:40:03:647936854Agent** START **Agent: Installing updates [CallerId = AutomaticUpdates]
2014-05-2703:40:03:647936854Agent* Updates to install = 1
Management Software
2014-05-2703:40:03:663936854Agent*Title = Configuration Manager Client (5.00.7958.1000)
2014-05-2703:40:03:663936854Agent*UpdateId = {8427071A-DA80-48C3-97DE-C9C528F73A2D}.1
2014-05-2703:40:03:679936854AgentWARNING: failed to calculate prior restore point time with error 0x80070002; setting restore point
2014-05-2703:40:03:7259369f0AUGetting featured update notifications.fIncludeDismissed = true
2014-05-2703:40:03:7259369f0AUNo featured updates available.
2014-05-2703:40:18:241936854DnldMgrPreparing update for install, updateId = {8427071A-DA80-48C3-97DE-C9C528F73A2D}.1.
Now let’s take a look at CCMsetup.log on the client computer:
Launch from folder C:WindowsSoftwareDistributionDownloadInstallccmsetup6/2/2014 3:00:54 AM3060 (0x0BF4)
CcmSetup version: 5.0.7958.1000ccmsetup6/2/2014 3:00:54 AM3060 (0x0BF4)
Running on 'Microsoft Windows 7 Enterprise ' (6.1.7601). Service Pack (1.0). SuiteMask = 272. Product Type = 18ccmsetup6/2/2014 3:01:01 AM3060 (0x0BF4)
Ccmsetup command line: 'C:WindowsSoftwareDistributionDownloadInstallccmsetup.exe'ccmsetup6/2/2014 3:01:02 AM3060 (0x0BF4)
Local Machine is joined to an AD domainccmsetup6/2/2014 3:01:02 AM3060 (0x0BF4)
Current AD forest name is Contoso.com, domain name is Contoso.comccmsetup6/2/2014 3:01:02 AM3060 (0x0BF4)
Domain joined client is in Intranetccmsetup6/2/2014 3:01:02 AM3060 (0x0BF4)
MSI log file:C:WindowsccmsetupLogsclient.msi.logccmsetup6/2/2014 3:01:09 AM3060 (0x0BF4)
MSI properties:SMSSITECODE='PR1' CCMHTTPPORT='80' CCMHTTPSPORT='443' CCMHTTPSSTATE='224' CCMFIRSTCERT='1'ccmsetup6/2/2014 3:01:09 AM3060 (0x0BF4)

As we can clearly see, CCMSetup is not calling any additional parameters with it. This simply means that all of the default parameters will be passed. Site and MP information will be fetched from Active Directory.
Shared-susdb-for-configuration-manager-software-update-points
Bindusar Kushwaha | Support Engineer | Microsoft GBS Management and Security Division
Get the latest System Center news onFacebookandTwitter:
System Center All Up: http://blogs.technet.com/b/systemcenter/
System Center – Configuration Manager Support Team blog: http://blogs.technet.com/configurationmgr/
System Center – Data Protection Manager Team blog: http://blogs.technet.com/dpm/
System Center – Orchestrator Support Team blog: http://blogs.technet.com/b/orchestrator/
System Center – Operations Manager Team blog: http://blogs.technet.com/momteam/
System Center – Service Manager Team blog: http://blogs.technet.com/b/servicemanager
System Center – Virtual Machine Manager Team blog: http://blogs.technet.com/scvmm
Windows Intune: http://blogs.technet.com/b/windowsintune/
WSUS Support Team blog: http://blogs.technet.com/sus/
The AD RMS blog: http://blogs.technet.com/b/rmssupp/
App-V Team blog: http://blogs.technet.com/appv/
MED-V Team blog: http://blogs.technet.com/medv/
Server App-V Team blog: http://blogs.technet.com/b/serverappv
The Forefront Endpoint Protection blog : http://blogs.technet.com/b/clientsecurity/
The Forefront Identity Manager blog : http://blogs.msdn.com/b/ms-identity-support/
The Forefront TMG blog: http://blogs.technet.com/b/isablog/
The Forefront UAG blog: http://blogs.technet.com/b/edgeaccessblog/

